full custody
ChainUp Custody is committed to providing private key management services for users of full custody wallets, ensuring that private keys are stored in secure devices based on HSM and SGX. Users can quickly access their custody assets through the web page and mobile application or Custody API. Our custody features are built on a highly scalable infrastructure that can quickly adapt to your business needs, meeting the continuous expansion of digital asset business.
- Highly Scalable SDK and API
ChainUp Custody’s service performance is highly scalable, allowing users to seamlessly integrate enterprise-level custody wallets into their applications. With plug-and-play SDKs and user-friendly APIs, users can quickly build and deploy custody applications without significant development costs.
- Transaction Strategy Engine
Our crypto coin transactions are subject to multifaceted risk control management. Users can set up detailed approval processes based on organizational roles and combine features such as transaction whitelists to achieve precise asset control and governance. This customizable internal control ecosystem helps mitigate risks such as operational errors or internal malicious behavior.
- User-Friendly Operations
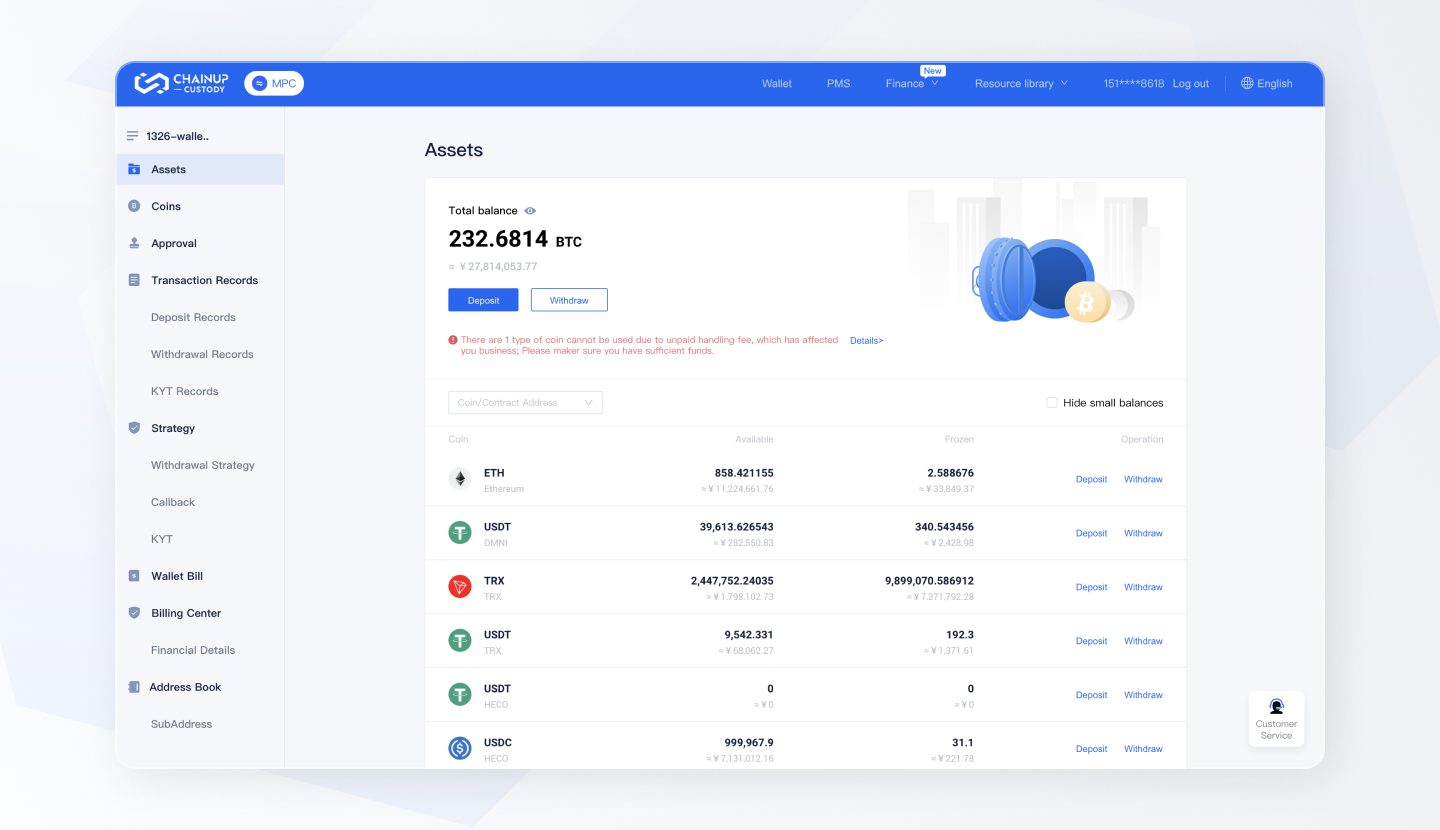
ChainUp Custody supports users in managing asset projects through the web page and mobile application, allowing users to access wallet information from anywhere. Through a simple and user-friendly interface, users can securely store and access assets from over 200 main chains and quickly manage team roles.
- Efficiency and Cost Reduction
We provide alliance transfer functionality for full custody users, ensuring that deposits and related transactions are timely, high-speed, and secure, unaffected by fluctuations in the blockchain network. The alliance transfer feature also offers lower market transaction fees, significantly reducing user operational costs and promoting the development of virtual asset businesses.
- International Security Certification
ChainUp Custody has obtained SOC2 Type1 and Type2 security system control verification reports, demonstrating our highest level of practical capabilities in information security management and customer data protection.
Was this page helpful?